<服务>OpenVPN
目录:
VPN
VPN介绍
VPN全称为虚拟专用网络,是依靠ISP和其他NSP,在公共网络创建专用的数据通信网络的技术,可以为企业之间,个人与企业之间提供安全的数据传输和隧道服务。
在VPN中任意两个服务器之间没有传统专网所需的端到端的物理链路,而是通过公共的网络资源动态生成的,可以理解为私有隧道技术在公共数据网络上模拟出来的和专网有同样特点的点到点的专线技术。
类似VPN的有PPTP,ipsec,ssh,lvs的tun模式(ip间隧道)
VPN的功能
可以帮助公司的远程用户,公司分支机构,商业合作伙伴以及供应商和自己公司内部网络之间建立可信的安全连接或者是局域网连接,确保数据的加密安全传输和业务访问,对于运维可以连接不同的机房为局域网,处理相关的业务流。
VPN的分类
根据功能大致可以分成4类
远程访问VPN服务
- 公司内部人员在外需要连接公司办公网络获取相关资源,例如域控制器等
- 运维人员在工作过程中连接到机房维护或者无内外网ip的服务器或网络设备
企业内部网络之间的VPN服务
- 在公司分支机构的局域网和公司总部之间VPN连接,可以用于地方部门之间进行业务结算
- 办公网络与机房环境之间进行数据同步或业务访问
- 异地容灾
不同企业之间
多个机房之间数据同步,业务访问和业务管理等
企业外部VPN服务
供应商,合作伙伴的LAN和本公司LAN之间建立VPN
访问国外网站
如标题所示,俗称翻墙>.<
翻墙的话用一个例子形容一下 个人主机地址192.168.0. 通过VPNserver进行翻墙 07
常见隧道协议
PPTP协议
- PPTP协议是点到点的隧道协议,基于拨号的PPP协议,使用PAP或CHAP之类的加密算法等,通过跨越基于TCP/IP协议的数据网络创建VPN实现传输;
- 实质是在IP头中通过ppp协议进行封装;
- Linux软件为pptp;
- 一般用于个人访问。
L2TP协议
- L2TP第二层隧道协议是IFTF基于L2F(Cisco的第二层转发协议)开发的PPTP的后续版本,是一种工业标准的Internet隧道协议
- PPTP只能在两点间建立相同的隧道,而L2TP可以建立多条
- PPTP不支持隧道验证,而L2TP支持,但是当L2TP或PPTP与IPSec共同使用的时候,由IPSec提供隧道验证
- PPTP要求是互联网络为IP网络,而L2TP只要求提供面向数据包的点对点连接即可
- L2TP的缺点为不能加密,所以经常与IPSec结合
IPSec协议
- IP安全协议,实质上是一套协议包。
- IPSec隧道协议是封装,路由与解封装的整个过程,隧道将原始的数据包隐藏或封装在数据包内部,新的数据包可能会有新的寻址和路由信息,从而在网络上传输,别人截获包也无法获取源地址和目的地址,到达目的地后再解除封装,路由到最终目的地址
- 两个机房或者企业之间就可以用此协议
- 当以隧道协议使用IPSec的时候,IP通讯只做封装,使用后主要是为了与不支持IPSec上的L2TP或PPTP的VPN隧道技术的路由器,网关和终端系统之间相互操作
SSLVPN
- SSL协议提供了数据私密性,端点验证,信息完全性的特点
- SSL协议由很多子协议组成,主要是握手协议和记录协议
- SSL协议握手协议是两端之间彼此确认并协商加密算法进行加密,记录协议利用握手协议生成的密钥加密和解密
- https就是用了SSL协议,OpenVPN也是应用了SSL协议
常见VPN开源软件
- PPTP VPN:windows默认支持PPTP VPN连接,属于点对点方式,适合用户拨号到公司,不过网络设备不支持PPTP会导致无法访问
- SSL VPN:SSLVPN即适合PPTP的应用场景又适合在企业之间或机房之间VPN不间断按需连接,开源产品为OpenVPN
- IPSec VPN: 多用于企业或者机房间,不过部署起来简单,开源产品为openswan
VPN选择建议
- 如果资金充足,可以选相关硬件产品,不错的有很多,例如防火墙,负载均衡等硬件产品都附带VPN,防火墙一般的10w+的价格,负载均衡例如F5就30w+。
- 开源产品扩展性强,甚至配置高可用,还可以二次开发,相应的改动等
- 个人拨号选择OpenVPN,如果不希望单独安装客户端才选择PPTP(不推荐),多个企业或机房可以用OpenVPN或IPSecVPN
OpenVPN
OpenVPN介绍
- OpenVPN是一个很好的开源软件,允许参与建立VPN的单点使用预设密钥,第三方证书或者用户名密码进行身份验证
- OpenVPN使用了openssl加密库,SSLv3/TLSv1协议
- OpenVPN能在Linux,xBSD,Mac OS和Windows上运行
- OpenVPN可以做访问控制
- OpenVPN应用于虚拟接口,不是基于web的软件,也不与IPSec以及其他软件包兼容,是一种C/S架构,需要单独客户端
依赖协议
- SSL是安全套接层是一种安全协议,在传输层中对网络通信进行加密;
- TLS是IETF将SSL进行标准化,与SSL协议一样也是在传输层进行加密;
- TLS1.0版本和SSL3.0版本在技术上差异很小。
SSL握手过程
- Client端向服务端发送消息,包括支持协议版本,客户端随机生成的随机数(用于生成会话密钥),支持的加密算法和压缩算法
- Server收到消息后会返回一个消息,包括确认使用的加密通信协议版本。如果浏览器和服务器支持的版本不一致,服务端关闭加密通信,并通过服务器生成随机数(用于生成会话密钥),确认使用的加密算法(例如RSA公钥,服务器证书)
- 通过前两步Client和Server之间确定了连接参数,客户端与服务端交换证书(这些证书通常基于x.509)
- Server端请求Client端公钥,Client证书则有双向身份验证,没有证书的时候随机生成
- Server端和Client端通过协商生成私钥,OpenVPN使用的是Diffie-Hellman交换生成私钥,双方各自使用私钥解密,所有其他的关键数据的加密均使用这个主密钥
OpenVPN工作原理
OpenVPN使用TLS加密协议(公开密钥的非对称加密),Server端与Client端有相同的CA签发证书,双方在交换证书中验证双方的合法性以决定是否建立VPN连接,然后使用对方的CA证书进行加密,所以只有对方的私钥才能进行解密,为了确保安全性,密钥定期进行改变。
OpenVPN多种身份验证方式
- 预享密钥
- 第三方证书和用户名密码
- 基于PKI的第三方证书
OpenVPN通信原理
OpenVPN通信都基于一个单一的端口(默认为1194),默认使用UDP通信协议(推荐用TCP协议),能够连通大多数服务器,尤其在NAT环境中。OpenVPN可以向客户端推送某些网络配置,例如IP地址,路由设置等,支持两个虚拟网络接口,Tun/Tap驱动,通过这两个接口可以建立三层IP隧道,或者虚拟二层以太网,会使用LZO算法数据压缩方式传输。
OpenVPN使用的是TCP/IP协议,就可以替代IPSec,当然是理想情况。
OpenVPN的核心技术就是虚拟网卡和SSL协议的实现,虚拟网卡是使用网络底层编程技术实现的一个驱动软件,安装后主机多出一个虚拟网卡,可以向其他网卡一样进行配置,服务程序可以在应用层打开虚拟网卡,如果应用软件向虚拟网卡发送数据,则虚拟网卡可以读取到该数据,如果是其他服务写数据到此虚拟网卡,应用软件也能读取到,即虚拟网卡在很多操作系统下都有响应的实现。
搭建VPN
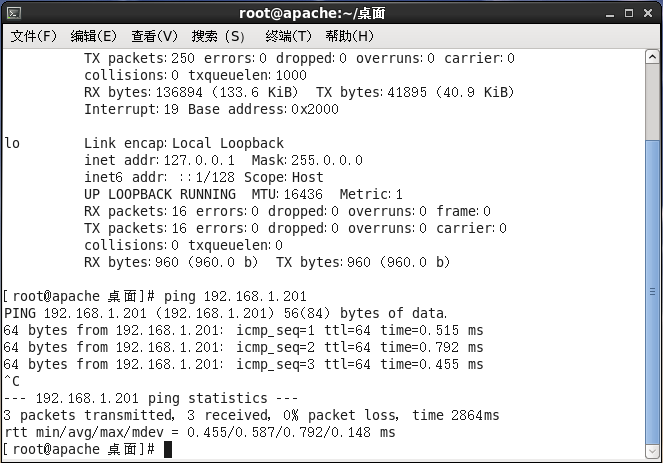
环境介绍
| 服务 | 外网IP | 内网IP |
|---|---|---|
| VPNServer | 192.168.0.201 | 192.168.1.201 |
| 内网机器 | 无 | 192.168.1.181 |
[root@why-1 ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.1.0 0.0.0.0 255.255.255.0 U 1 0 0 eth1
192.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 eth0
0.0.0.0 192.168.0.1 0.0.0.0 UG 0 0 0 eth0
[root@why-1 ~]# ping baidu.com
PING baidu.com (123.125.114.144) 56(84) bytes of data.
64 bytes from 123.125.114.144: icmp_seq=1 ttl=56 time=26.6 ms
64 bytes from 123.125.114.144: icmp_seq=2 ttl=56 time=4.19 ms
^C
--- baidu.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1348ms
rtt min/avg/max/mdev = 4.190/15.419/26.648/11.229 ms
[root@why-1 ~]# ping 192.168.1.181
PING 192.168.1.181 (192.168.1.181) 56(84) bytes of data.
64 bytes from 192.168.1.181: icmp_seq=1 ttl=64 time=1.95 ms
64 bytes from 192.168.1.181: icmp_seq=2 ttl=64 time=0.367 ms
^C
--- 192.168.1.181 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1982ms
rtt min/avg/max/mdev = 0.367/1.159/1.951/0.792 ms
模拟环境
[root@why-1 ~]# ntpdate pool.ntp.org
18 Feb 02:14:23 ntpdate[29738]: step time server 203.135.184.123 offset 327699.983501 sec
[root@why-1 ~]# echo '*/5 * * * * /usr/sbin/ntpdate pool.ntp.org >/dev/null 2>&1' >>/var/spool/cron/root
[root@why-1 ~]# cat !$
cat /var/spool/cron/root
*/5 * * * * /usr/sbin/ntpdate pool.ntp.org >/dev/null 2>&1
[root@why-1 ~]# wget http://www.oberhumer.com/opensource/lzo/download/lzo-2.06.tar.gz
[root@why-1 ~]# tar xf lzo-2.06.tar.gz
[root@why-1 ~]# cd lzo-2.06
[root@why-1 lzo-2.06]# ./configure
[root@why-1 lzo-2.06]# make
[root@why-1 lzo-2.06]# make install
[root@why-1 ~]# wget http://www.openvpn.net/release/openvpn-2.2.2.tar.gz
[root@why-1 ~]# cd openvpn-2.2.2
[root@why-1 openvpn-2.2.2]# ./configure --with-lzo-headers=/usr/local/include --with-lzo-lib=/usr/local/lib
[root@why-1 openvpn-2.2.2]# make
[root@why-1 openvpn-2.2.2]# make install
[root@why-1 openvpn-2.2.2]# which openvpn
/usr/local/sbin/openvpn
注:http://www.openvpn.net/release/openvpn-2.2.2.tar.gz无法正常打开,需要翻墙或者去CSDN等网站下载。
配置VPNserver
[root@why-1 openvpn-2.2.2]# cd easy-rsa/2.0/
[root@why-1 2.0]# cp vars vars.old
[root@why-1 2.0]# vi vars
export KEY_COUNTRY="US"
export KEY_PROVINCE="CA"
export KEY_CITY="SanFrancisco"
export KEY_ORG="Fort-Funston"
export KEY_EMAIL="me@myhost.mydomain"
export KEY_EMAIL=mail@host.domain
export KEY_CN=changeme
export KEY_NAME=changeme
export KEY_OU=changeme
export PKCS11_MODULE_PATH=changeme
export PKCS11_PIN=1234
改为
export KEY_COUNTRY="CN"
export KEY_PROVINCE="BJ"
export KEY_CITY="Beijing"
export KEY_ORG="why"
export KEY_EMAIL="93216193@qq.com"
export KEY_EMAIL=93216193@qq.com
export KEY_CN=why-1 #这里要填VPN服务器的FQDN
export KEY_NAME=why
export KEY_OU=why
export PKCS11_MODULE_PATH=changeme
export PKCS11_PIN=1234
[root@why-1 2.0]# . vars #配置生效
NOTE: If you run ./clean-all, I will be doing a rm -rf on /root/openvpn-2.2.2/easy-rsa/2.0/keys
创建CA证书
[root@why-1 2.0]# ./clean-all #清除所有CA证书
[root@why-1 2.0]# ./build-ca #生成CA证书
Generating a 1024 bit RSA private key
....++++++
.........................................................................++++++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]: <-直接回车使用[]中的默认值,也可以填写新的值回车
State or Province Name (full name) [BJ]: <-直接回车使用[]中的默认值,也可以填写新的值回车
Locality Name (eg, city) [Beijing]: <-直接回车使用[]中的默认值,也可以填写新的值回车
Organization Name (eg, company) [why]: <-直接回车使用[]中的默认值,也可以填写新的值回车
Organizational Unit Name (eg, section) [why]: <-直接回车使用[]中的默认值,也可以填写新的值回车
Common Name (eg, your name or your server's hostname) [why-1]: <-直接回车使用[]中的默认值,也可以填写新的值回车(这里要填VPN服务器的FQDN)
Name [why]: <-直接回车使用[]中的默认值,也可以填写新的值回车
Email Address [93216193@qq.com]: <-直接回车使用[]中的默认值,也可以填写新的值回车
[root@why-1 2.0]# ll keys/
总用量 12
-rw-r--r-- 1 root root 1261 2月 14 07:07 ca.crt #证书
-rw------- 1 root root 916 2月 14 07:07 ca.key #私钥
-rw-r--r-- 1 root root 0 2月 14 07:04 index.txt
-rw-r--r-- 1 root root 3 2月 14 07:04 serial
生成服务端密钥
[root@why-1 2.0]# ./build-key-server server
Generating a 1024 bit RSA private key
......++++++
.++++++
writing new private key to 'server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]: #国家名
State or Province Name (full name) [BJ]: #省市名
Locality Name (eg, city) [Beijing]: #城市名
Organization Name (eg, company) [why]: #组织名
Organizational Unit Name (eg, section) [why]: #单元名
Common Name (eg, your name or your server's hostname) [server]: #主机名
Name [why]: #用户名
Email Address [93216193@qq.com]: #Email
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456 #发送证书请求的密码
An optional company name []:why #可选公司名
Using configuration from /root/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'Beijing'
organizationName :PRINTABLE:'why'
organizationalUnitName:PRINTABLE:'why'
commonName :PRINTABLE:'server'
name :PRINTABLE:'why'
emailAddress :IA5STRING:'93216193@qq.com'
Certificate is to be certified until Feb 16 11:01:18 2027 GMT (3650 days)
Sign the certificate? [y/n]:y #是否确认填写的内容
1 out of 1 certificate requests certified, commit? [y/n]y #是否提交
Write out database with 1 new entries
Data Base Updated
[root@why-1 2.0]# ll keys/
总用量 40
-rw-r--r-- 1 root root 3929 2月 18 19:01 01.pem
-rw-r--r-- 1 root root 1269 2月 18 18:59 ca.crt
-rw------- 1 root root 920 2月 18 18:59 ca.key
-rw-r--r-- 1 root root 111 2月 18 19:01 index.txt
-rw-r--r-- 1 root root 21 2月 18 19:01 index.txt.attr
-rw-r--r-- 1 root root 3 2月 18 19:01 serial
-rw-r--r-- 1 root root 3929 2月 18 19:01 server.crt
-rw-r--r-- 1 root root 753 2月 18 19:01 server.csr
-rw------- 1 root root 916 2月 18 19:01 server.key
生成客户端证书和key文件
如果需要建立多个客户端证书,重复一下步骤即可,只需要修改Common Name项的名称。在OpenVPN中,每一个登录的VPN客户端都要有一个证书,每个证书在同一时刻只能有一个客户端连接,如果两台机器安装相同的证书连接服务器,都可以拨上,但是只有第一个拨上的能连接网络。
[root@why-1 2.0]# ./build-key why
Generating a 1024 bit RSA private key
..................................++++++
.................................++++++
writing new private key to 'why.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [Beijing]:
Organization Name (eg, company) [why]:
Organizational Unit Name (eg, section) [why]:
Common Name (eg, your name or your server's hostname) [why]:
Name [why]:
Email Address [93216193@qq.com]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:why
Using configuration from /root/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'Beijing'
organizationName :PRINTABLE:'why'
organizationalUnitName:PRINTABLE:'why'
commonName :PRINTABLE:'why'
name :PRINTABLE:'why'
emailAddress :IA5STRING:'93216193@qq.com'
Certificate is to be certified until Feb 16 14:32:21 2027 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@why-1 2.0]# ll keys/
总用量 64
-rw-r--r-- 1 root root 3929 2月 18 19:01 01.pem
-rw-r--r-- 1 root root 3801 2月 18 22:32 02.pem
-rw-r--r-- 1 root root 1269 2月 18 18:59 ca.crt
-rw------- 1 root root 920 2月 18 18:59 ca.key
-rw-r--r-- 1 root root 219 2月 18 22:32 index.txt
-rw-r--r-- 1 root root 21 2月 18 22:32 index.txt.attr
-rw-r--r-- 1 root root 3 2月 18 22:32 serial
-rw-r--r-- 1 root root 3929 2月 18 19:01 server.crt
-rw-r--r-- 1 root root 753 2月 18 19:01 server.csr
-rw------- 1 root root 916 2月 18 19:01 server.key
-rw-r--r-- 1 root root 3801 2月 18 22:32 why.crt
-rw-r--r-- 1 root root 749 2月 18 22:32 why.csr
-rw------- 1 root root 916 2月 18 22:32 why.key
通过build-key创建的用户,拨号的时候是不需要密码的,不过我们可以改密码或者加密码,通过build-key-pass创建的用户需要加密码
[root@why-1 2.0]# ./build-key-pass mabiao
Generating a 1024 bit RSA private key
.........++++++
........++++++
writing new private key to 'mabiao.key'
Enter PEM pass phrase: #定义密码,输入后不显示(why123)
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [Beijing]:
Organization Name (eg, company) [why]:
Organizational Unit Name (eg, section) [why]:
Common Name (eg, your name or your server's hostname) [mabiao]:
Name [why]:
Email Address [93216193@qq.com]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:why
Using configuration from /root/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'Beijing'
organizationName :PRINTABLE:'why'
organizationalUnitName:PRINTABLE:'why'
commonName :PRINTABLE:'mabiao'
name :PRINTABLE:'why'
emailAddress :IA5STRING:'93216193@qq.com'
Certificate is to be certified until Feb 16 14:37:44 2027 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
利用算法生成协议文件
生成传输进行密钥交换时使用到的交换密钥协议文件,这个文件一定要在OpenVPNserver上生成。
[root@why-1 2.0]# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long time
.............................+..............................................................................................+..................+.........................................+...........................................................+..............+...............................+...........................................+....................................+....+...................................................................................................................................+.+..+..............+...............+...................+................+........................................................+...............................................................+........+.+...............................................................+....................................................................................................+.........................................................................................................................................+..........+.....+.........................................................................................+...+..+.........................+.....................+.......+........+...............................................+.............+...........+..........................................+....................+...............+..............+................................+.........+...........+...................................................................................+............................+..............................................+...............................................+..........................................................................+...................................................................+........................................................+........................................+....................................................................+.........................................+.............+...........................................................................................................................................................................................+............................................................+.........................................................................+.......................+.............+....................................+..........+...........................+.............+..........................................+......................+............+..........................+................+.....+...............................+.......++*++*++*
[root@why-1 2.0]# ll keys/dh1024.pem
-rw-r--r-- 1 root root 245 2月 18 22:48 keys/dh1024.pem
详解文件内容
[root@why-1 2.0]# ll keys/
总用量 84
-rw-r--r-- 1 root root 3929 2月 18 19:01 01.pem
-rw-r--r-- 1 root root 3801 2月 18 22:32 02.pem
-rw-r--r-- 1 root root 3808 2月 18 22:37 03.pem
-rw-r--r-- 1 root root 1269 2月 18 18:59 ca.crt #ca证书,Server端和所有Client端都要有的文件
-rw------- 1 root root 920 2月 18 18:59 ca.key #ca key文件,Server端文件
-rw-r--r-- 1 root root 245 2月 18 22:48 dh1024.pem #协议文件,只在Server端
-rw-r--r-- 1 root root 330 2月 18 22:37 index.txt
-rw-r--r-- 1 root root 21 2月 18 22:37 index.txt.attr
-rw-r--r-- 1 root root 21 2月 18 22:32 index.txt.attr.old
-rw-r--r-- 1 root root 219 2月 18 22:32 index.txt.old
-rw-r--r-- 1 root root 3808 2月 18 22:37 mabiao.crt
-rw-r--r-- 1 root root 753 2月 18 22:37 mabiao.csr
-rw------- 1 root root 1041 2月 18 22:37 mabiao.key
-rw-r--r-- 1 root root 3 2月 18 22:37 serial
-rw-r--r-- 1 root root 3 2月 18 22:32 serial.old
-rw-r--r-- 1 root root 3929 2月 18 19:01 server.crt #Server端的证书
-rw-r--r-- 1 root root 753 2月 18 19:01 server.csr
-rw------- 1 root root 916 2月 18 19:01 server.key #Server端的key
-rw-r--r-- 1 root root 3801 2月 18 22:32 why.crt #Client端why的证书
-rw-r--r-- 1 root root 749 2月 18 22:32 why.csr
-rw------- 1 root root 916 2月 18 22:32 why.key #Client端why的key
生成HMAC firewall
[root@why-1 2.0]# openvpn --genkey --secret keys/ta.key [root@why-1 2.0]# ll !$ ll keys/ta.key -rw------- 1 root root 636 2月 18 23:00 keys/ta.key
VPN服务端命令
- vars 脚本是用来创建环境变量,设置所需要的变量的脚本,可以理解为模板文件
- clean-all 脚本是用来生成ca证书和密钥文件所需要的文件及目录
- build-ca 脚本生成ca证书和密钥(交互的方式)
- build-dh 脚本生成Diffie-Hellman文件(交互的方式)
- build-key-server 脚本生成Server端证书和密钥(交互的方式)
- build-key 脚本生成Client端证书和密钥(交互的方式)
- build-key-pass 脚本生成Client带密码的证书和密钥(交互的方式)
配置文件详解
[root@why-1 2.0]# cp -ap keys !$ #cp -ap目录和文件属性保持一致进行拷贝
cp -ap keys /etc/openvpn
[root@why-1 openvpn]# grep -vE ";|#|^$" server.conf
port 1194 #监听端口,默认为1194,为了安全起见修改一下
proto udp #监听协议,当并发访问多时,推荐使用tcp
dev tun #vpn server的模式采用路由模式,可选tap或tun,这两个模式博主也不太清楚
ca ca.crt #ca证书,要配置在和server.conf相对的目录下或绝对路径
cert server.crt #Server端证书,要配置在和server.conf相对的目录下或绝对路径
dh dh1024.pem #协议文件,要配置在和server.conf相对的目录下或绝对路径
server 10.8.0.0 255.255.255.0 #Client端拨号之后,Server端按照该地址池分配给Client端的IP,类似DHCP的地址池,该地址段不要与任何网络地址段冲突或者重复
ifconfig-pool-persist ipp.txt
keepalive 10 120 #每10s ping一次,若120s未收到包则认定Client端断线
comp-lzo #开启压缩功能
persist-key #VPN超时后,当重启启动VPN后,保持上一次使用的私钥,而不重新读取私钥
persist-tun #通过keepalive检测VPN超时后,当重启启动VPN后,保持tun或tap设备自动连接
status openvpn-status.log #OpenVPN日志状态信息
verb 3 #指定日志文件冗余
相比上述内容,我们需要添加的配置内容
local 121.42.37.139 #OpenVPN服务启动的时候监控的IP,Client端需要通过该IP访问Server端。
push "route 10.0.0.0 255.255.255.0" #VPN Server端推送到Client端的路由,10.0.0.0为内网网段,255.255.255.0为子网掩码,如果有多个网段可以,写多行push。
client-to-client #允许多个VPN Client端互相通信
duplicate-cn #允许多个Client端使用同一个账户连接
log /var/log/openvpn.log #日志文件
修改配置文件
[root@why-1 openvpn]# grep -vE ";|#|^$" server.conf > tmp.log
[root@why-1 openvpn]# cat tmp.log > server.conf
[root@why-1 openvpn]# vi server.conf
[root@why-1 openvpn]# diff server.conf tmp.log
1,2c1,2
< port 54321
< proto tcp
---
> port 1194
> proto udp
4,7c4,6
< ca keys/ca.crt
< cert keys/server.crt
< key keys/server.key
< dh keys/dh1024.pem
---
> ca ca.crt
> cert server.crt
> dh dh1024.pem
16,20d14
< local 192.168.0.201
< push "route 192.168.1.0 255.255.255.0"
< client-to-client
< duplicate-cn
< log /var/log/openvpn.log
VPNServer端环境修改
防火墙允许OpenVPN端口
[root@why-1 openvpn]# service iptables stop
iptables:将链设置为政策 ACCEPT:filter [确定]
iptables:清除防火墙规则: [确定]
iptables:正在卸载模块: [确定]
确认防火墙转发和内核转发
[root@why-1 openvpn]# iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@why-1 openvpn]# sysctl -p
net.ipv4.ip_forward = 0
net.ipv4.conf.default.rp_filter = 1
net.ipv4.conf.default.accept_source_route = 0
kernel.sysrq = 0
kernel.core_uses_pid = 1
net.ipv4.tcp_syncookies = 1
net.bridge.bridge-nf-call-ip6tables = 0
net.bridge.bridge-nf-call-iptables = 0
net.bridge.bridge-nf-call-arptables = 0
kernel.msgmnb = 65536
kernel.msgmax = 65536
kernel.shmmax = 68719476736
kernel.shmall = 4294967296
[root@why-1 openvpn]# sed -i "s/net.ipv4.ip_forward = 0/net.ipv4.ip_forward = 1/g" /etc/sysctl.conf
[root@why-1 openvpn]# sysctl -p
net.ipv4.ip_forward = 1
net.ipv4.conf.default.rp_filter = 1
net.ipv4.conf.default.accept_source_route = 0
kernel.sysrq = 0
kernel.core_uses_pid = 1
net.ipv4.tcp_syncookies = 1
net.bridge.bridge-nf-call-ip6tables = 0
net.bridge.bridge-nf-call-iptables = 0
net.bridge.bridge-nf-call-arptables = 0
kernel.msgmnb = 65536
kernel.msgmax = 65536
kernel.shmmax = 68719476736
kernel.shmall = 4294967296
启动OpenVPN
[root@why-1 openvpn]# /usr/local/sbin/openvpn --config /etc/openvpn/server.conf &
[1] 2380
[root@why-1 openvpn]# netstat -nlptu | grep 54321
tcp 0 0 192.168.0.201:54321 0.0.0.0:* LISTEN 2380/openvpn
[root@why-1 openvpn]# tail /var/log/openvpn.log
Sun Feb 19 00:56:21 2017 /sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.2
Sun Feb 19 00:56:21 2017 Data Channel MTU parms [ L:1544 D:1450 EF:44 EB:135 ET:0 EL:0 AF:3/1 ]
Sun Feb 19 00:56:21 2017 Listening for incoming TCP connection on 192.168.0.201:54321
Sun Feb 19 00:56:21 2017 TCPv4_SERVER link local (bound): 192.168.0.201:54321
Sun Feb 19 00:56:21 2017 TCPv4_SERVER link remote: [undef]
Sun Feb 19 00:56:21 2017 MULTI: multi_init called, r=256 v=256
Sun Feb 19 00:56:21 2017 IFCONFIG POOL: base=10.8.0.4 size=62
Sun Feb 19 00:56:21 2017 IFCONFIG POOL LIST
Sun Feb 19 00:56:21 2017 MULTI: TCP INIT maxclients=1024 maxevents=1028
Sun Feb 19 00:56:21 2017 Initialization Sequence Completed
[root@why-1 openvpn]# ifconfig #可以看到多一块网卡
eth0 Link encap:Ethernet HWaddr 00:0C:29:98:5B:B7
inet addr:192.168.0.201 Bcast:192.168.0.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe98:5bb7/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:4103 errors:0 dropped:0 overruns:0 frame:0
TX packets:2353 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:348678 (340.5 KiB) TX bytes:324872 (317.2 KiB)
Interrupt:19 Base address:0x2000
eth1 Link encap:Ethernet HWaddr 00:0C:29:98:5B:C1
inet addr:192.168.1.201 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe98:5bc1/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:701 errors:0 dropped:0 overruns:0 frame:0
TX packets:18 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:53368 (52.1 KiB) TX bytes:1964 (1.9 KiB)
Interrupt:16 Base address:0x2080
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:16 errors:0 dropped:0 overruns:0 frame:0
TX packets:16 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1248 (1.2 KiB) TX bytes:1248 (1.2 KiB)
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.1 P-t-P:10.8.0.2 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
添加vpn到init.d管理
[root@why-1 openvpn]# cp ~/openvpn-2.2.2/sample-scripts/openvpn.init /etc/init.d/openvpn
[root@why-1 openvpn]# chmod 700 !$
chmod 700 /etc/init.d/openvpn
[root@why-1 openvpn]# chkconfig --add openvpn
[root@why-1 openvpn]# chkconfig --list openvpn
openvpn 0:off 1:off 2:off 3:on 4:on 5:on 6:off
[root@why-1 openvpn]# vi /etc/init.d/openvpn #如果/etc/openvpn目录下有多个.conf为后缀的文件需要进行此操作
148行改为
for c in `/bin/ls server.conf 2>/dev/null`; do
[root@why-1 openvpn]# pkill openvpn
[root@why-1 openvpn]# service openvpn start
正在启动 openvpn: [确定]
[1]+ Done /usr/local/sbin/openvpn --config /etc/openvpn/server.conf
windows端OpenVPN配置
安装windows VPN 客户端
下载连接http://swupdate.openvpn.org/community/releases/openvpn-2.2.2-install.exe
选择I Agree
选择Next
可是选择默认的目录,也可以自定义,但是要记住目录位置
进行安装
windows会反馈是否信任此软件
安装完成
[root@why-1 openvpn]# cd keys/
[root@why-1 keys]# sz -y ca.crt why.crt why.key ../client.conf
将这些目录放到安装OpenVPN的目录的config下
[root@why-1 keys]# cd ..
[root@why-1 openvpn]# egrep -v "^$|^#|^;" client.conf
client
dev tun
proto udp
remote my-server-1 1194
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
ns-cert-type server
comp-lzo
verb 3
[root@why-1 openvpn]# cp client.conf client.conf.old
[root@why-1 openvpn]# egrep -v "^$|^#|^;" client.conf > tmp_client.log
[root@why-1 openvpn]# cat tmp_client.log > client.conf
[root@why-1 openvpn]# vi client.conf
[root@why-1 openvpn]# cat client.conf
client
dev tun
proto tcp
remote 192.168.0.201 54321
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert why.crt
key why.key
ns-cert-type server
comp-lzo
verb 3
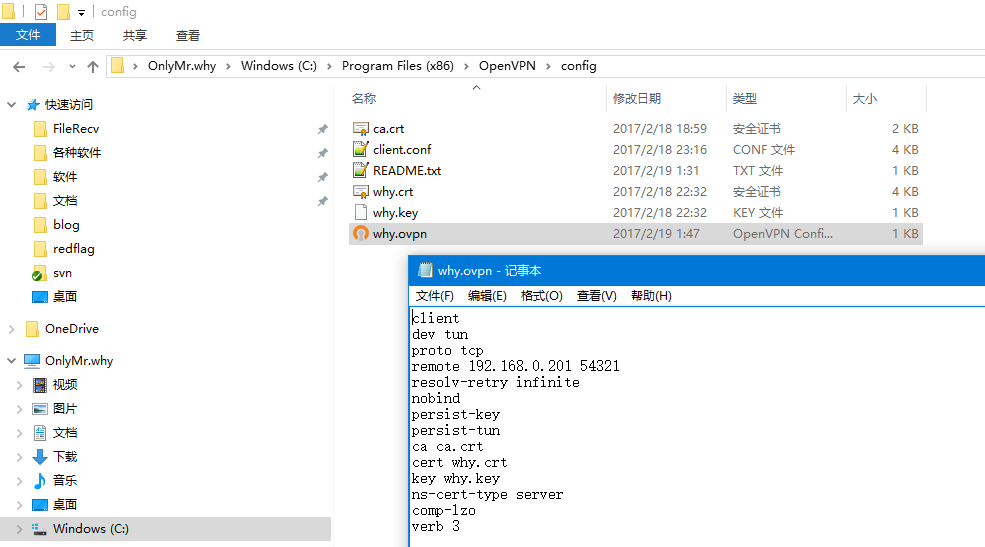
在windows下的config目录下创建why.ovpn文件,并将上述写入到文件中
OpenVPN拨号
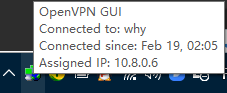
安装完OpenVPN在桌面会有一个OpenVPN GUI的快捷方式,点击开启,会在右下方看到openvpn的图标
右击选着Connect进行连接即可,我们只有一个Client,这里不会显示名字,如果有多个Client即显示多个名字
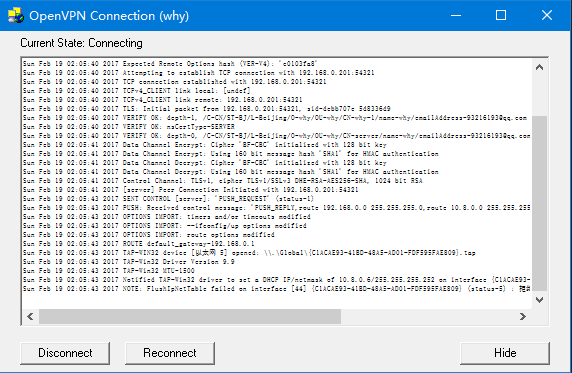
点击Connect之后会出现下面的提示,然后消失
右下角的图标也变为绿色,红色和黄色代表不成功
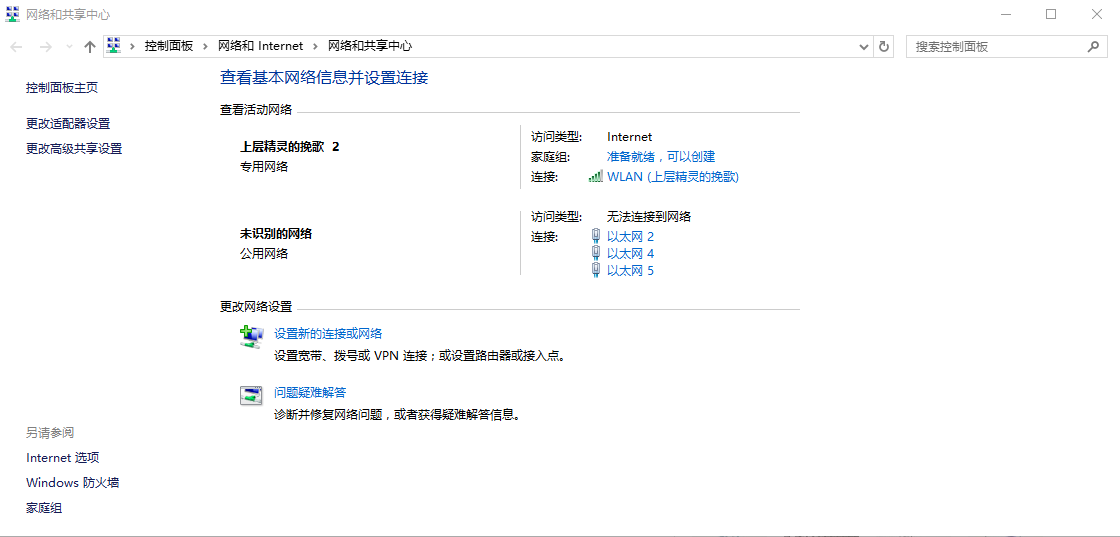
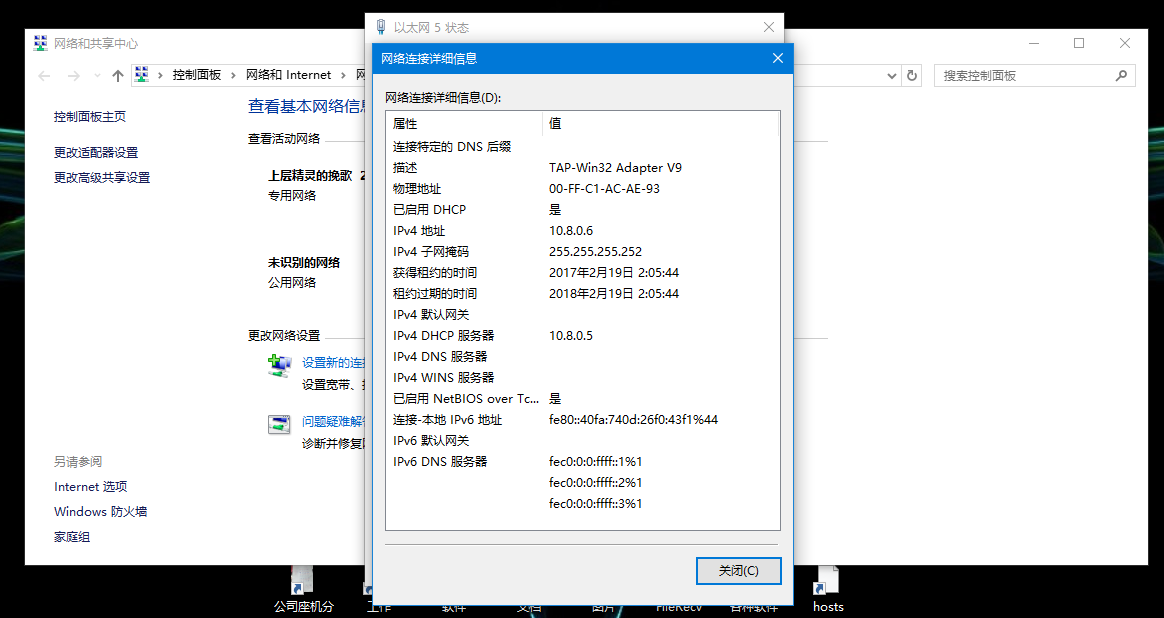
这个10.8.0.6即为分配给Client端的IP地址,我们也可以看一下我们的网络,多了一个以太网5,以太网2和以太网4分别是VMware的NAT模式网卡和主机模式网卡
对应IP也为10.8.0.6
[root@why-1 openvpn]# tail /var/log/openvpn.log
Sun Feb 19 02:05:36 2017 192.168.0.104:63796 Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sun Feb 19 02:05:36 2017 192.168.0.104:63796 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Feb 19 02:05:36 2017 192.168.0.104:63796 Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sun Feb 19 02:05:36 2017 192.168.0.104:63796 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Feb 19 02:05:36 2017 192.168.0.104:63796 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Sun Feb 19 02:05:36 2017 192.168.0.104:63796 [why] Peer Connection Initiated with 192.168.0.104:63796
Sun Feb 19 02:05:36 2017 why/192.168.0.104:63796 MULTI: Learn: 10.8.0.6 -> why/192.168.0.104:63796
Sun Feb 19 02:05:36 2017 why/192.168.0.104:63796 MULTI: primary virtual IP for why/192.168.0.104:63796: 10.8.0.6
Sun Feb 19 02:05:39 2017 why/192.168.0.104:63796 PUSH: Received control message: 'PUSH_REQUEST'
Sun Feb 19 02:05:39 2017 why/192.168.0.104:63796 SENT CONTROL [why]: 'PUSH_REPLY,route 192.168.0.0 255.255.255.0,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5' (status=1)
在win7下就没有问题了,在win10会出现这个问题,可以通过双击openvpn图标看到。
Sun Feb 19 03:00:42 2017 OpenVPN 2.2.2 Win32-MSVC++ [SSL] [LZO2] [PKCS11] built on Dec 15 2011
Sun Feb 19 03:00:42 2017 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables
Sun Feb 19 03:00:42 2017 LZO compression initialized
Sun Feb 19 03:00:42 2017 Control Channel MTU parms [ L:1544 D:140 EF:40 EB:0 ET:0 EL:0 ]
Sun Feb 19 03:00:42 2017 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sun Feb 19 03:00:42 2017 Data Channel MTU parms [ L:1544 D:1450 EF:44 EB:135 ET:0 EL:0 AF:3/1 ]
Sun Feb 19 03:00:42 2017 Local Options hash (VER=V4): '69109d17'
Sun Feb 19 03:00:42 2017 Expected Remote Options hash (VER=V4): 'c0103fa8'
Sun Feb 19 03:00:42 2017 Attempting to establish TCP connection with 192.168.0.201:54321
Sun Feb 19 03:00:42 2017 TCP connection established with 192.168.0.201:54321
Sun Feb 19 03:00:42 2017 TCPv4_CLIENT link local: [undef]
Sun Feb 19 03:00:42 2017 TCPv4_CLIENT link remote: 192.168.0.201:54321
Sun Feb 19 03:00:42 2017 TLS: Initial packet from 192.168.0.201:54321, sid=57fcd123 dd8018ef
Sun Feb 19 03:00:42 2017 VERIFY OK: depth=1, /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=why-1/name=why/emailAddress=93216193@qq.com
Sun Feb 19 03:00:42 2017 VERIFY OK: nsCertType=SERVER
Sun Feb 19 03:00:42 2017 VERIFY OK: depth=0, /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=server/name=why/emailAddress=93216193@qq.com
Sun Feb 19 03:00:42 2017 Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sun Feb 19 03:00:42 2017 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Feb 19 03:00:42 2017 Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sun Feb 19 03:00:42 2017 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Feb 19 03:00:42 2017 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Sun Feb 19 03:00:42 2017 [server] Peer Connection Initiated with 192.168.0.201:54321
Sun Feb 19 03:00:44 2017 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Sun Feb 19 03:00:44 2017 PUSH: Received control message: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5'
Sun Feb 19 03:00:44 2017 OPTIONS IMPORT: timers and/or timeouts modified
Sun Feb 19 03:00:44 2017 OPTIONS IMPORT: --ifconfig/up options modified
Sun Feb 19 03:00:44 2017 OPTIONS IMPORT: route options modified
Sun Feb 19 03:00:44 2017 ROUTE default_gateway=192.168.0.1
Sun Feb 19 03:00:45 2017 TAP-WIN32 device [以太网 5] opened: \\.\Global\{C1ACAE93-41BD-48A5-AD01-FDF595FAE809}.tap
Sun Feb 19 03:00:45 2017 TAP-Win32 Driver Version 9.9
Sun Feb 19 03:00:45 2017 TAP-Win32 MTU=1500
Sun Feb 19 03:00:45 2017 Notified TAP-Win32 driver to set a DHCP IP/netmask of 10.8.0.6/255.255.255.252 on interface {C1ACAE93-41BD-48A5-AD01-FDF595FAE809} [DHCP-serv: 10.8.0.5, lease-time: 31536000]
Sun Feb 19 03:00:45 2017 NOTE: FlushIpNetTable failed on interface [44] {C1ACAE93-41BD-48A5-AD01-FDF595FAE809} (status=5) : 拒绝访问。
Sun Feb 19 03:00:50 2017 TEST ROUTES: 2/2 succeeded len=2 ret=1 a=0 u/d=up
Sun Feb 19 03:00:50 2017 C:\WINDOWS\system32\route.exe ADD 192.168.1.0 MASK 255.255.255.0 10.8.0.5
Sun Feb 19 03:00:50 2017 ROUTE: route addition failed using CreateIpForwardEntry: 拒绝访问。 [status=5 if_index=44]
Sun Feb 19 03:00:50 2017 Route addition via IPAPI failed [adaptive]
Sun Feb 19 03:00:50 2017 Route addition fallback to route.exe
请求的操作需要提升。
Sun Feb 19 03:00:50 2017 ERROR: Windows route add command failed [adaptive]: returned error code 1
Sun Feb 19 03:00:50 2017 C:\WINDOWS\system32\route.exe ADD 10.8.0.0 MASK 255.255.255.0 10.8.0.5
Sun Feb 19 03:00:50 2017 ROUTE: route addition failed using CreateIpForwardEntry: 拒绝访问。 [status=5 if_index=44]
Sun Feb 19 03:00:50 2017 Route addition via IPAPI failed [adaptive]
Sun Feb 19 03:00:50 2017 Route addition fallback to route.exe
请求的操作需要提升。
Sun Feb 19 03:00:50 2017 ERROR: Windows route add command failed [adaptive]: returned error code 1
Sun Feb 19 03:00:50 2017 Initialization Sequence Completed
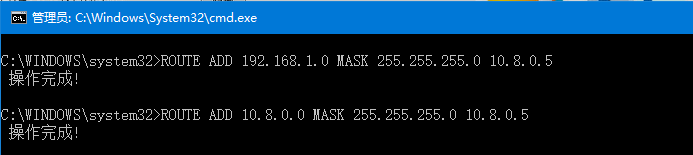
是OpenVPN执行添加路由没有权限,我这边通过以管理员身份执行cmd.exe,执行了以下命令
ROUTE ADD 192.168.1.0 MASK 255.255.255.0 10.8.0.5
ROUTE ADD 10.8.0.0 MASK 255.255.255.0 10.8.0.5
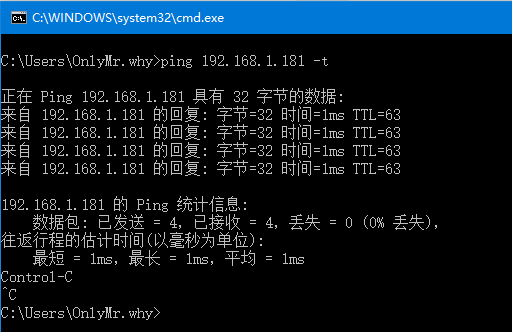
现在我们的拨号就是成功的了
连接内网机器
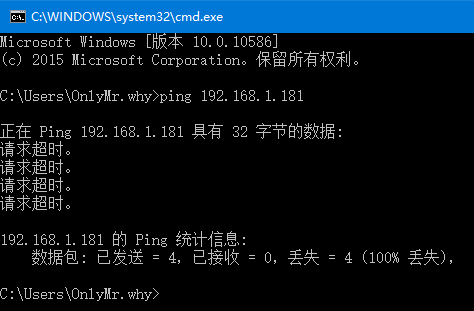
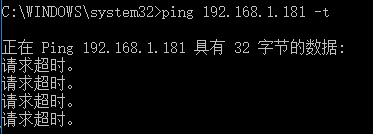
但是我们仍然无法连接到内网机器,根据TCP/IP协议,我们发送的数据包源地址10.8.0.6,目的地址192.168.1.181
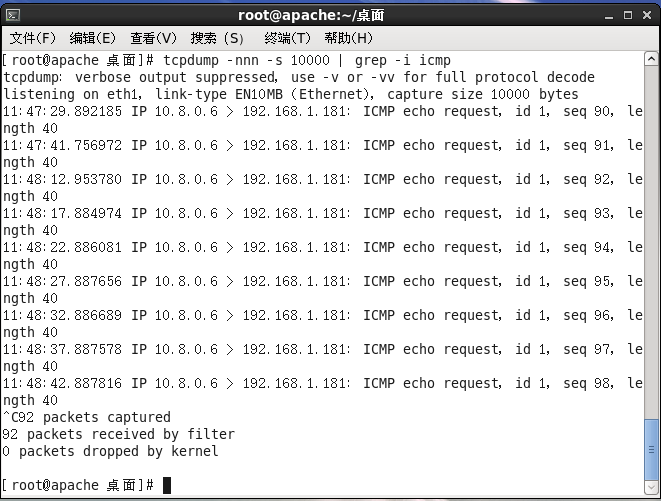
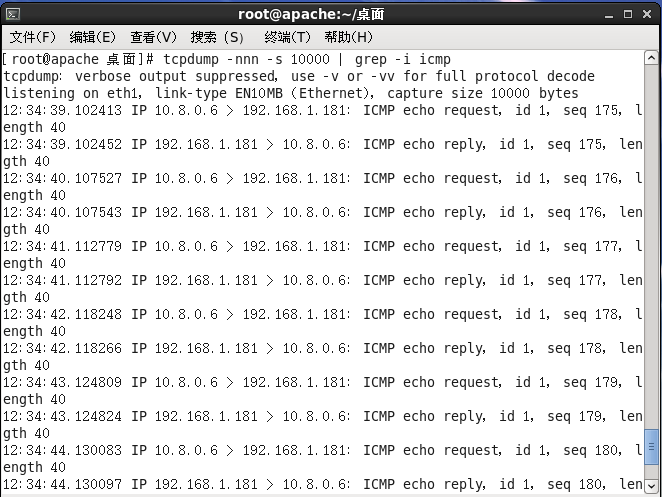
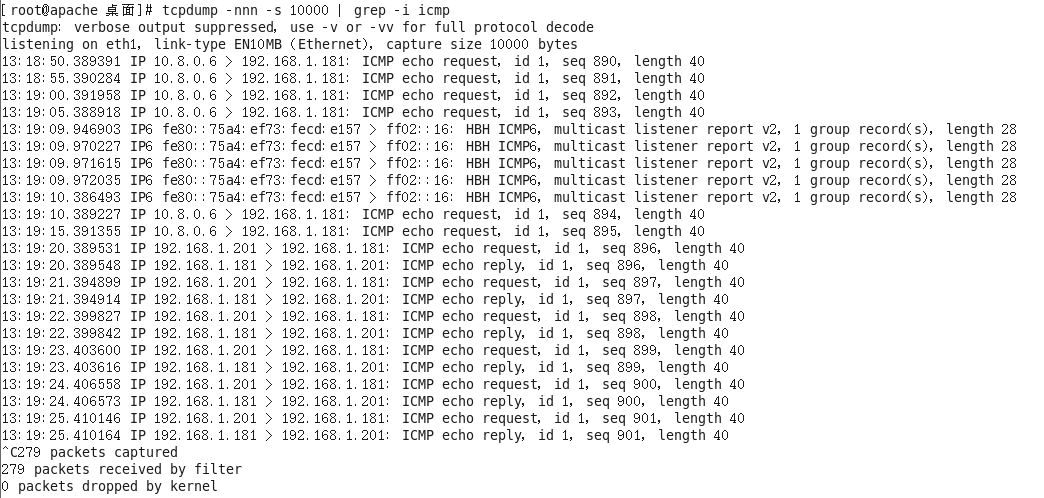
我们通过tcpdump在192.168.1.181进行抓包
可以看到是可以抓到10.8.0.6发来的请求包,我们只需要进行添加192.168.1.181返回给10.8.0.6的路由或者能路由到10.8.0.6的默认网关即可
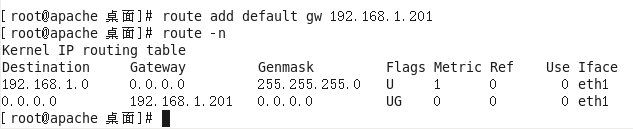
最简单的就是OpenVPNServer的内网IP可以路由到10.8.0.6上,在内网机器192.168.1.181上添加路由到192.168.1.201上即可
route add default gw 192.168.1.201
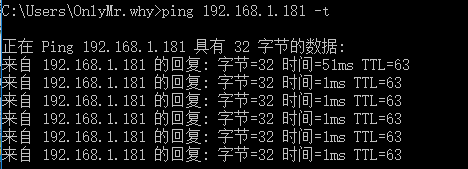
再尝试ping 192.168.1.201可以ping通
内网机器也可以抓到请求和应答两种包
如果内网机器有默认网关不为VPNServer的内网IP,可以添加路由
route add -net 10.8.0.0/24 gw 192.168.1.201
只不过所有的内网机器都要添加路由
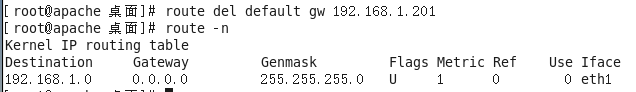
当然还有另一种方式实现,就是在VPNServer端做NAT,我们先把之前的网关删掉
route del default gw 192.168.1.201
在192.168.1.181做NAT的目的是把10.8.0.0/24网段的数据包的源地址改为192.168.1.201
[root@why-1 openvpn]# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth1 -j SNAT --to-source 192.168.1.201
[root@why-1 openvpn]# iptables -t nat -L -n
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 10.8.0.0/24 0.0.0.0/0 to:192.168.1.201
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
可以在抓包的过程中明显的看到在没有NAT的时候,数据包的源地址为10.8.0.6,NAT后变为了192.168.1.201
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth1 -j MASQUERADE
启动防火墙
这个不是重点,只是提一下,OpenVPN提供了一个配置防火墙的脚本,可以进行一些修改使用
[root@why-1 openvpn]# cd ~/openvpn-2.2.2/sample-config-files/
[root@why-1 sample-config-files]# ll firewall.sh
-rwxrwxr-x 1 mysql mysql 3562 Nov 25 2011 firewall.sh
如果是原始的防火墙规则,需要允许FORWARD即可
查看登录状态文件
[root@why-1 sample-config-files]# cat /etc/openvpn/openvpn-status.log
OpenVPN CLIENT LIST
Updated,Sun Feb 19 05:13:28 2017
Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since
why,192.168.0.104:50004,300619,212103,Sun Feb 19 03:33:36 2017
ROUTING TABLE
Virtual Address,Common Name,Real Address,Last Ref
10.8.0.6,why,192.168.0.104:50004,Sun Feb 19 05:05:36 2017
GLOBAL STATS
Max bcast/mcast queue length,0
END
OpenVPN证书吊销
需要进行吊销的有三种情况
- 需要证书丢失
- 忘记密码
- 不想让该证书登录
撤销证书的操作
[root@why-1 ~]# cd openvpn-2.2.2/easy-rsa/2.0/
[root@why-1 2.0]# source vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /root/openvpn-2.2.2/easy-rsa/2.0/keys
[root@why-1 2.0]# vi openssl-1.0.0.cnf
注释掉一下内容
[ pkcs11_section ]
engine_id = pkcs11
dynamic_path = /usr/lib/engines/engine_pkcs11.so
MODULE_PATH = $ENV::PKCS11_MODULE_PATH
PIN = $ENV::PKCS11_PIN
init = 0
如果上面的操作在有些版本需要进行,另外修改的文件根据我们的openssl版本决定。如果不修改可能会导致吊销报错,当然也可能是报错,仍然吊销成功
[root@why-1 2.0]# ./revoke-full why
Using configuration from /root/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
Revoking Certificate 02.
Data Base Updated
Using configuration from /root/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
why.crt: C = CN, ST = BJ, L = Beijing, O = why, OU = why, CN = why, name = why, emailAddress = 93216193@qq.com
error 23 at 0 depth lookup:certificate revoked
当前即报错但吊销成功
[root@why-1 2.0]# ll keys/crl.pem
-rw-r--r-- 1 root root 536 2月 19 16:24 keys/crl.pem
[root@why-1 2.0]# cat keys/crl.pem
-----BEGIN X509 CRL-----
MIIBYjCBzDANBgkqhkiG9w0BAQQFADCBhjELMAkGA1UEBhMCQ04xCzAJBgNVBAgT
AkJKMRAwDgYDVQQHEwdCZWlqaW5nMQwwCgYDVQQKEwN3aHkxDDAKBgNVBAsTA3do
eTEOMAwGA1UEAxMFd2h5LTExDDAKBgNVBCkTA3doeTEeMBwGCSqGSIb3DQEJARYP
OTMyMTYxOTNAcXEuY29tFw0xNzAyMTkwODI0MTlaFw0xNzAzMjEwODI0MTlaMBQw
EgIBAhcNMTcwMjE5MDgyNDE5WjANBgkqhkiG9w0BAQQFAAOBgQC9ZFqQoGqjfVm8
x30+0s+eNqkFFH2MJBhk+fMf5q3LxYU7gXQriE3RhkjZr8nWAWWdFPFV+sX+1qFF
/pea1nTfGKGHyl05cOOvYas5l4UV/OG1NkajhU3uys5w5V0rO8JSfGdUwdCRl9qp
pfs4WCEnqz0lTmXQeiLiQt6VJMrngQ==
-----END X509 CRL-----
[root@why-1 2.0]# cat keys/index.txt
V 270216110118Z 01 unknown /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=server/name=why/emailAddress=93216193@qq.com
R 270216143221Z 170219082419Z 02 unknown /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=why/name=why/emailAddress=93216193@qq.com
V 270216143744Z 03 unknown /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=mabiao/name=why/emailAddress=93216193@qq.com
可以看到R的为吊销的
配置吊销
[root@why-1 2.0]# cp keys/crl.pem /etc/openvpn/keys/
[root@why-1 2.0]# vi /etc/openvpn/server.conf
[root@why-1 2.0]# tail -1 !$
tail -1 /etc/openvpn/server.conf
crl-verify keys/crl.pem
[root@why-1 2.0]# service openvpn stop
正在关闭openvpn: [确定]
[root@why-1 2.0]# service openvpn start
正在启动 openvpn: [确定]
[root@why-1 2.0]# ps -ef | grep openvpn
root 3780 1 0 16:33 ? 00:00:00 /usr/local/sbin/openvpn --daemon --writepid /var/run/openvpn/server.pid --config server.conf --cd /etc/openvpn
root 3786 3664 0 16:34 pts/0 00:00:00 grep openvpn
这样OpenVPN进行登录的时候就会读取吊销列表中的客户端,并禁止其拨入
再通过windows端登录就会出现以下错误
Sun Feb 19 16:34:51 2017 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables
Sun Feb 19 16:34:51 2017 Re-using SSL/TLS context
Sun Feb 19 16:34:51 2017 LZO compression initialized
Sun Feb 19 16:34:51 2017 Control Channel MTU parms [ L:1544 D:140 EF:40 EB:0 ET:0 EL:0 ]
Sun Feb 19 16:34:51 2017 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sun Feb 19 16:34:51 2017 Data Channel MTU parms [ L:1544 D:1450 EF:44 EB:135 ET:0 EL:0 AF:3/1 ]
Sun Feb 19 16:34:51 2017 Local Options hash (VER=V4): '69109d17'
Sun Feb 19 16:34:51 2017 Expected Remote Options hash (VER=V4): 'c0103fa8'
Sun Feb 19 16:34:51 2017 Attempting to establish TCP connection with 192.168.0.201:54321
Sun Feb 19 16:34:51 2017 TCP connection established with 192.168.0.201:54321
Sun Feb 19 16:34:51 2017 TCPv4_CLIENT link local: [undef]
Sun Feb 19 16:34:51 2017 TCPv4_CLIENT link remote: 192.168.0.201:54321
Sun Feb 19 16:34:51 2017 TLS: Initial packet from 192.168.0.201:54321, sid=00360fdb bb3b7490
Sun Feb 19 16:34:52 2017 VERIFY OK: depth=1, /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=why-1/name=why/emailAddress=93216193@qq.com
Sun Feb 19 16:34:52 2017 VERIFY OK: nsCertType=SERVER
Sun Feb 19 16:34:52 2017 VERIFY OK: depth=0, /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=server/name=why/emailAddress=93216193@qq.com
Sun Feb 19 16:34:52 2017 Connection reset, restarting [-1]
Sun Feb 19 16:34:52 2017 TCP/UDP: Closing socket
Sun Feb 19 16:34:52 2017 SIGUSR1[soft,connection-reset] received, process restarting
Sun Feb 19 16:34:52 2017 Restart pause, 5 second(s)
提示socket关闭,连接重置。图标也一直为黄色的。这个可以通过按住ctrl和滚动鼠标放大。
Linux端OpenVPN
时间同步
[root@why-2 ~]# ntpdate pool.ntp.org
19 Feb 17:06:26 ntpdate[10320]: step time server 85.199.214.101 offset 138593.058561 sec
[root@why-2 ~]# echo '*/5 * * * * /usr/sbin/ntpdate pool.ntp.org >/dev/null 2>&1' >>/var/spool/cron/root
安装依赖
[root@why-2 ~]# wget http://www.oberhumer.com/opensource/lzo/download/lzo-2.06.tar.gz
[root@why-2 ~]# tar xf lzo-2.06.tar.gz
[root@why-2 ~]# cd lzo-2.06
[root@why-2 lzo-2.06]# ./configure
[root@why-2 lzo-2.06]# make
[root@why-2 lzo-2.06]# make install
安装服务
[root@why-2 lzo-2.06]# cd ..
[root@why-2 ~]# tar xf openvpn-2.2.2.tar.gz
[root@why-2 ~]# cd openvpn-2.2.2
[root@why-2 openvpn-2.2.2]# ./configure --with-lzo-headers=/usr/local/include --with-lzo-lib=/usr/local/lib
[root@why-2 openvpn-2.2.2]# make
[root@why-2 openvpn-2.2.2]# make install
[root@why-2 openvpn-2.2.2]# mkdir /etc/openvpn
[root@why-2 openvpn-2.2.2]# cd /etc/openvpn
[root@why-2 openvpn]# ll
total 24
-rw-r--r-- 1 root root 213 Feb 19 01:31 README.txt
-rw-r--r-- 1 root root 1269 Feb 18 18:59 ca.crt
-rw-r--r-- 1 root root 3426 Feb 18 23:16 client.conf
-rw-r--r-- 1 root root 3801 Feb 18 22:32 why.crt
-rw-r--r-- 1 root root 916 Feb 18 22:32 why.key
-rw-r--r-- 1 root root 190 Feb 19 01:47 why.ovpn
[root@why-2 openvpn]# mv client.conf client.conf.old
[root@why-2 openvpn]# mv why.ovpn client.conf
[root@why-2 openvpn]# ll
total 24
-rw-r--r-- 1 root root 213 Feb 19 01:31 README.txt
-rw-r--r-- 1 root root 1269 Feb 18 18:59 ca.crt
-rw-r--r-- 1 root root 190 Feb 19 01:47 client.conf
-rw-r--r-- 1 root root 3426 Feb 18 23:16 client.conf.old
-rw-r--r-- 1 root root 3801 Feb 18 22:32 why.crt
-rw-r--r-- 1 root root 916 Feb 18 22:32 why.key
启动服务并检测
[root@why-2 openvpn]# /usr/local/sbin/openvpn --config /etc/openvpn/client.conf &
[1] 21249
[root@why-2 openvpn]# Sun Feb 19 17:30:25 2017 OpenVPN 2.2.2 x86_64-unknown-linux-gnu [SSL] [LZO2] [EPOLL] [eurephia] built on Feb 19 2017
Sun Feb 19 17:30:25 2017 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables
Sun Feb 19 17:30:25 2017 WARNING: file 'why.key' is group or others accessible
Sun Feb 19 17:30:25 2017 LZO compression initialized
Sun Feb 19 17:30:25 2017 Control Channel MTU parms [ L:1544 D:140 EF:40 EB:0 ET:0 EL:0 ]
Sun Feb 19 17:30:25 2017 Socket Buffers: R=[87380->131072] S=[16384->131072]
Sun Feb 19 17:30:25 2017 Data Channel MTU parms [ L:1544 D:1450 EF:44 EB:135 ET:0 EL:0 AF:3/1 ]
Sun Feb 19 17:30:25 2017 Local Options hash (VER=V4): '69109d17'
Sun Feb 19 17:30:25 2017 Expected Remote Options hash (VER=V4): 'c0103fa8'
Sun Feb 19 17:30:25 2017 Attempting to establish TCP connection with 192.168.0.201:54321 [nonblock]
Sun Feb 19 17:30:26 2017 TCP connection established with 192.168.0.201:54321
Sun Feb 19 17:30:26 2017 TCPv4_CLIENT link local: [undef]
Sun Feb 19 17:30:26 2017 TCPv4_CLIENT link remote: 192.168.0.201:54321
Sun Feb 19 17:30:26 2017 TLS: Initial packet from 192.168.0.201:54321, sid=fd0dc178 171f480b
Sun Feb 19 17:30:26 2017 VERIFY OK: depth=1, /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=why-1/name=why/emailAddress=93216193@qq.com
Sun Feb 19 17:30:26 2017 VERIFY OK: nsCertType=SERVER
Sun Feb 19 17:30:26 2017 VERIFY OK: depth=0, /C=CN/ST=BJ/L=Beijing/O=why/OU=why/CN=server/name=why/emailAddress=93216193@qq.com
Sun Feb 19 17:30:26 2017 Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sun Feb 19 17:30:26 2017 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Feb 19 17:30:26 2017 Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sun Feb 19 17:30:26 2017 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun Feb 19 17:30:26 2017 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Sun Feb 19 17:30:26 2017 [server] Peer Connection Initiated with 192.168.0.201:54321
Sun Feb 19 17:30:29 2017 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Sun Feb 19 17:30:29 2017 PUSH: Received control message: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.10 10.8.0.9'
Sun Feb 19 17:30:29 2017 OPTIONS IMPORT: timers and/or timeouts modified
Sun Feb 19 17:30:29 2017 OPTIONS IMPORT: --ifconfig/up options modified
Sun Feb 19 17:30:29 2017 OPTIONS IMPORT: route options modified
Sun Feb 19 17:30:29 2017 ROUTE default_gateway=192.168.0.1
Sun Feb 19 17:30:29 2017 TUN/TAP device tun0 opened
Sun Feb 19 17:30:29 2017 TUN/TAP TX queue length set to 100
Sun Feb 19 17:30:29 2017 /sbin/ifconfig tun0 10.8.0.10 pointopoint 10.8.0.9 mtu 1500
Sun Feb 19 17:30:29 2017 /sbin/route add -net 192.168.1.0 netmask 255.255.255.0 gw 10.8.0.9
Sun Feb 19 17:30:29 2017 /sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.9
Sun Feb 19 17:30:29 2017 Initialization Sequence Completed
[root@why-2 openvpn]# echo $?
0
[root@why-2 openvpn]# ps -ef | grep openvpn
root 21249 10293 0 17:30 pts/2 00:00:00 /usr/local/sbin/openvpn --config /etc/openvpn/client.conf
root 21260 10293 0 17:31 pts/2 00:00:00 grep openvpn
[root@why-2 openvpn]# ifconfig tun0
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.10 P-t-P:10.8.0.9 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
[root@why-2 openvpn]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
10.8.0.9 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
10.8.0.0 10.8.0.9 255.255.255.0 UG 0 0 0 tun0
192.168.1.0 10.8.0.9 255.255.255.0 UG 0 0 0 tun0
192.168.0.0 0.0.0.0 255.255.255.0 U 1 0 0 eth0
0.0.0.0 192.168.0.1 0.0.0.0 UG 0 0 0 eth0
[root@why-2 openvpn]# ping 192.168.1.181
PING 192.168.1.181 (192.168.1.181) 56(84) bytes of data.
64 bytes from 192.168.1.181: icmp_seq=1 ttl=63 time=4.05 ms
64 bytes from 192.168.1.181: icmp_seq=2 ttl=63 time=1.50 ms
64 bytes from 192.168.1.181: icmp_seq=3 ttl=63 time=1.75 ms
^C
--- 192.168.1.181 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2114ms
rtt min/avg/max/mdev = 1.505/2.439/4.057/1.149 ms
VPNServer端检测
[root@why-1 ~]# cat /etc/openvpn/openvpn-status.log
OpenVPN CLIENT LIST
Updated,Sun Feb 19 17:40:40 2017
Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since
why,192.168.0.202:38011,7250,8966,Sun Feb 19 17:30:25 2017
why,192.168.0.105:57288,129256,72476,Sun Feb 19 16:40:56 2017
ROUTING TABLE
Virtual Address,Common Name,Real Address,Last Ref
10.8.0.10,why,192.168.0.202:38011,Sun Feb 19 17:30:27 2017
10.8.0.6,why,192.168.0.105:57288,Sun Feb 19 17:40:33 2017
GLOBAL STATS
Max bcast/mcast queue length,0
END
[root@why-1 ~]# tcpdump -i eth0 -nnn -s 10000 'port 54321 and src host 192.168.0.202'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 10000 bytes
17:50:21.612403 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [.], ack 1123985921, win 792, options [nop,nop,TS val 437946639 ecr 23880679], length 0
17:50:21.612920 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [P.], seq 0:55, ack 1, win 792, options [nop,nop,TS val 437946639 ecr 23880679], length 55
17:50:21.925660 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [P.], seq 55:182, ack 1, win 792, options [nop,nop,TS val 437946952 ecr 23880720], length 127
17:50:21.969902 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [.], ack 128, win 792, options [nop,nop,TS val 437946996 ecr 23880996], length 0
17:50:22.928264 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [P.], seq 182:309, ack 128, win 792, options [nop,nop,TS val 437947955 ecr 23880996], length 127
17:50:22.930275 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [.], ack 255, win 792, options [nop,nop,TS val 437947957 ecr 23881997], length 0
17:50:23.929980 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [P.], seq 309:436, ack 255, win 792, options [nop,nop,TS val 437948956 ecr 23881997], length 127
17:50:23.931683 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [.], ack 382, win 792, options [nop,nop,TS val 437948958 ecr 23882998], length 0
17:50:24.932320 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [P.], seq 436:563, ack 382, win 792, options [nop,nop,TS val 437949959 ecr 23882998], length 127
17:50:24.933440 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [.], ack 509, win 792, options [nop,nop,TS val 437949960 ecr 23884000], length 0
17:50:25.935010 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [P.], seq 563:690, ack 509, win 792, options [nop,nop,TS val 437950961 ecr 23884000], length 127
17:50:25.936491 IP 192.168.0.202.38011 > 192.168.0.201.54321: Flags [.], ack 636, win 792, options [nop,nop,TS val 437950963 ecr 23885003], length 0
^C
12 packets captured
12 packets received by filter
0 packets dropped by kernel
这样就安装完成了
可能出现的问题
Sun Feb 19 23:13:16 2017 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables
Sun Feb 19 23:13:16 2017 WARNING: file 'yanwei.key' is group or others accessible
Sun Feb 19 23:13:16 2017 Cannot load CA certificate file ca.crt path (null) (SSL_CTX_load_verify_locations): error:02001002:system library:fopen:No such file or directory: error:2006D080:BIO routines:BIO_new_file:no such file: error:0B084002:x509 certificate routines:X509_load_cert_crl_file:system lib
Sun Feb 19 23:13:16 2017 Exiting
如果出现Cannot load certificate file ***.crt可以按照提示添加--script-security 2在client.conf文件中并修改client.conf的文件名,即可。如果不改名还会报错,可能是个bug。
多个机房或多个企业就适用于该场景,例如办公环境和生产环境推送数据,生产环境之间跨机房备份等,这样就可以取消所有不需要连接外网的IP地址。还有一个架构,MySQL远程写,然后远程主库同步到本地从库,读的过程从本地读取数据的架构也可以通过OpenVPN进行实现。
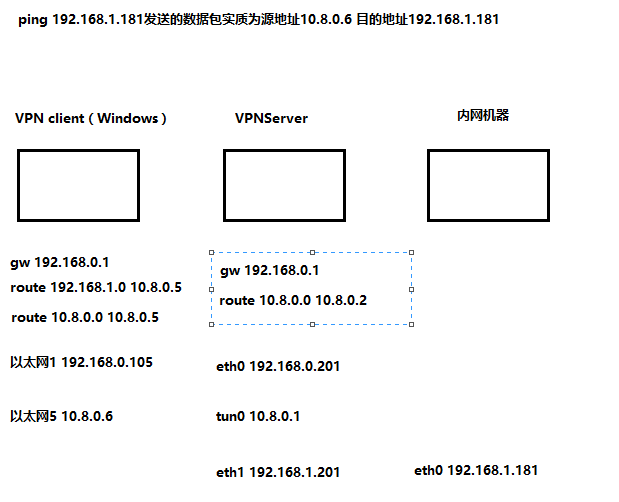
OpenVPN进行路由原理
上述例子,以windows环境为例
- 数据包从VPNClient端发出源地址10.8.0.6,目地址为192.168.1.181,网段为192.168.1.0,交给10.8.0.5网关处理
- 在OpenVPN启动的时候自动添加了路由10.8.0.5收到数据包交给0.0.0.0处理
- 0.0.0.0走默认网关到192.198.0.1处理,达到192.168.0.201机器,即VPNServer机器
- VPNServer通过192.168.1.201IP所在网段广播到192.168.1.181机器,从而传给192.168.1.181机器到目的地址内网机器,然后进行返回包,此时的包源地址为192.168.1.181,目的地址为10.8.0.6
- 不论是指定了默认网关为192.168.1.201还是把10.8.0.0/24网段的数据包路由到192.168.1.201原理是一样的,交给192.168.1.201机器处理
- VPNServer端把目的地址为10.8.0.6,根据路由交给10.8.0.2网关处理
- 10.8.0.2的路由也指向了0.0.0.0处理
- 0.0.0.0走默认网关到192.168.0.1处理,达到了192.168.0.105主机,也就是IP地址为10.8.0.6的地址,完后了一次ping
提供两个网上的博文仅供参考 使用openvpn连通多个机房内网 openVPN 打通IDC机房与公司内网
总结
OpenVPN是为了解决功能问题,而非性能问题,如果大数据量的传输需要拉专线了。所以这个VPN隧道也需要检测防止大文件传输。