<博客建立历程>阿里云建站18——免费的HTTPS
目录:
Let's Encrypt SSL证书
Let's Encrypt是一个免费、开放,自动化的证书颁发机构,由ISRG(Internet Security Research Group)运作。
ISRG 是一个关注网络安全的公益组织,其赞助商从非商业组织到财富100强公司都有,包括Mozilla、Akamai、Cisco、Facebook,密歇根大学等等。ISRG 以消除资金,技术领域的障碍,全面推进加密连接成为互联网标配为自己的使命。
Let's Encrypt 项目于2012年由 Mozilla 的两个员工发起,2014年11年对外宣布公开,2015年12月3日开启公测。
Let's Encrypt 目前处于公测期间,文档,工具还不完善,请谨慎用于生产环境。
安装方式
Let's Encrypy目前只支持类Unix系统,需要python2.6或2.7,暂时不支持python3
以下演示环境为python2.6,使用官方推荐的letsencry-auto脚本进行安装
下载脚本
[root@why ~]# git clone https://github.com/letsencrypt/letsencrypt
Initialized empty Git repository in /root/letsencrypt/.git/
remote: Counting objects: 47908, done.
remote: Compressing objects: 100% (122/122), done.
remote: Total 47908 (delta 143), reused 157 (delta 101), pack-reused 47685
Receiving objects: 100% (47908/47908), 14.62 MiB | 3.78 MiB/s, done.
Resolving deltas: 100% (34231/34231), done.
进行安装
[root@why ~]# cd letsencrypt
[root@why letsencrypt]# ./letsencrypt-auto --help
Bootstrapping dependencies for RedHat-based OSes... (you can skip this with --no-bootstrap)
yum is /usr/bin/yum
Loaded plugins: security
Setting up Install Process
Package gcc-4.4.7-18.el6.x86_64 already installed and latest version
Package openssl-1.0.1e-57.el6.x86_64 already installed and latest version
Package openssl-devel-1.0.1e-57.el6.x86_64 already installed and latest version
Package python-2.6.6-66.el6_8.x86_64 already installed and latest version
Package python-devel-2.6.6-66.el6_8.x86_64 already installed and latest version
Package python-pip-7.1.0-1.el6.noarch already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package augeas-libs.x86_64 0:1.0.0-10.el6 will be installed
---> Package ca-certificates.noarch 0:2014.1.98-65.0.el6_5 will be updated
---> Package ca-certificates.noarch 0:2017.2.14-65.0.1.el6_9 will be an update
---> Package libffi-devel.x86_64 0:3.0.5-3.2.el6 will be installed
---> Package mod_ssl.x86_64 1:2.2.15-60.el6.centos.4 will be installed
--> Processing Dependency: httpd = 2.2.15-60.el6.centos.4 for package: 1:mod_ssl-2.2.15-60.el6.centos.4.x86_64
---> Package python-tools.x86_64 0:2.6.6-66.el6_8 will be installed
--> Processing Dependency: tkinter = 2.6.6-66.el6_8 for package: python-tools-2.6.6-66.el6_8.x86_64
---> Package python-virtualenv.noarch 0:1.10.1-1.el6 will be installed
---> Package redhat-rpm-config.noarch 0:9.0.3-42.el6.centos will be updated
---> Package redhat-rpm-config.noarch 0:9.0.3-51.el6.centos will be an update
--> Running transaction check
---> Package httpd.x86_64 0:2.2.15-54.el6.centos will be updated
---> Package httpd.x86_64 0:2.2.15-60.el6.centos.4 will be an update
--> Processing Dependency: httpd-tools = 2.2.15-60.el6.centos.4 for package: httpd-2.2.15-60.el6.centos.4.x86_64
---> Package tkinter.x86_64 0:2.6.6-66.el6_8 will be installed
--> Processing Dependency: libtk8.5.so()(64bit) for package: tkinter-2.6.6-66.el6_8.x86_64
--> Processing Dependency: libtcl8.5.so()(64bit) for package: tkinter-2.6.6-66.el6_8.x86_64
--> Processing Dependency: libTix.so()(64bit) for package: tkinter-2.6.6-66.el6_8.x86_64
--> Running transaction check
---> Package httpd-tools.x86_64 0:2.2.15-54.el6.centos will be updated
---> Package httpd-tools.x86_64 0:2.2.15-60.el6.centos.4 will be an update
---> Package tcl.x86_64 1:8.5.7-6.el6 will be installed
---> Package tix.x86_64 1:8.4.3-5.el6 will be installed
---> Package tk.x86_64 1:8.5.7-5.el6 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
==============================================================================================================================================================================================================================================================================
Package Arch Version Repository Size
==============================================================================================================================================================================================================================================================================
Installing:
augeas-libs x86_64 1.0.0-10.el6 base 314 k
libffi-devel x86_64 3.0.5-3.2.el6 base 18 k
mod_ssl x86_64 1:2.2.15-60.el6.centos.4 updates 98 k
python-tools x86_64 2.6.6-66.el6_8 base 871 k
python-virtualenv noarch 1.10.1-1.el6 epel 1.3 M
Updating:
ca-certificates noarch 2017.2.14-65.0.1.el6_9 updates 1.3 M
redhat-rpm-config noarch 9.0.3-51.el6.centos base 60 k
Installing for dependencies:
tcl x86_64 1:8.5.7-6.el6 base 1.9 M
tix x86_64 1:8.4.3-5.el6 base 252 k
tk x86_64 1:8.5.7-5.el6 base 1.4 M
tkinter x86_64 2.6.6-66.el6_8 base 258 k
Updating for dependencies:
httpd x86_64 2.2.15-60.el6.centos.4 updates 839 k
httpd-tools x86_64 2.2.15-60.el6.centos.4 updates 80 k
Transaction Summary
==============================================================================================================================================================================================================================================================================
Install 9 Package(s)
Upgrade 4 Package(s)
Total download size: 8.6 M
Downloading Packages:
(1/13): augeas-libs-1.0.0-10.el6.x86_64.rpm | 314 kB 00:00
(2/13): ca-certificates-2017.2.14-65.0.1.el6_9.noarch.rpm | 1.3 MB 00:01
(3/13): httpd-2.2.15-60.el6.centos.4.x86_64.rpm | 839 kB 00:00
(4/13): httpd-tools-2.2.15-60.el6.centos.4.x86_64.rpm | 80 kB 00:00
(5/13): libffi-devel-3.0.5-3.2.el6.x86_64.rpm | 18 kB 00:00
(6/13): mod_ssl-2.2.15-60.el6.centos.4.x86_64.rpm | 98 kB 00:00
(7/13): python-tools-2.6.6-66.el6_8.x86_64.rpm | 871 kB 00:00
(8/13): python-virtualenv-1.10.1-1.el6.noarch.rpm | 1.3 MB 00:01
(9/13): redhat-rpm-config-9.0.3-51.el6.centos.noarch.rpm | 60 kB 00:00
(10/13): tcl-8.5.7-6.el6.x86_64.rpm | 1.9 MB 00:01
(11/13): tix-8.4.3-5.el6.x86_64.rpm | 252 kB 00:00
(12/13): tk-8.5.7-5.el6.x86_64.rpm | 1.4 MB 00:01
(13/13): tkinter-2.6.6-66.el6_8.x86_64.rpm | 258 kB 00:00
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Total 1.0 MB/s | 8.6 MB 00:08
Running rpm_check_debug
Running Transaction Test
Transaction Test Succeeded
Running Transaction
Installing : 1:tcl-8.5.7-6.el6.x86_64 1/17
Installing : 1:tk-8.5.7-5.el6.x86_64 2/17
Installing : 1:tix-8.4.3-5.el6.x86_64 3/17
Installing : tkinter-2.6.6-66.el6_8.x86_64 4/17
Updating : httpd-tools-2.2.15-60.el6.centos.4.x86_64 5/17
Updating : httpd-2.2.15-60.el6.centos.4.x86_64 6/17
Installing : 1:mod_ssl-2.2.15-60.el6.centos.4.x86_64 7/17
Installing : python-tools-2.6.6-66.el6_8.x86_64 8/17
Updating : ca-certificates-2017.2.14-65.0.1.el6_9.noarch 9/17
Updating : redhat-rpm-config-9.0.3-51.el6.centos.noarch 10/17
Installing : augeas-libs-1.0.0-10.el6.x86_64 11/17
Installing : python-virtualenv-1.10.1-1.el6.noarch 12/17
Installing : libffi-devel-3.0.5-3.2.el6.x86_64 13/17
Cleanup : ca-certificates-2014.1.98-65.0.el6_5.noarch 14/17
Cleanup : redhat-rpm-config-9.0.3-42.el6.centos.noarch 15/17
Cleanup : httpd-2.2.15-54.el6.centos.x86_64 16/17
Cleanup : httpd-tools-2.2.15-54.el6.centos.x86_64 17/17
Verifying : 1:mod_ssl-2.2.15-60.el6.centos.4.x86_64 1/17
Verifying : 1:tk-8.5.7-5.el6.x86_64 2/17
Verifying : libffi-devel-3.0.5-3.2.el6.x86_64 3/17
Verifying : python-virtualenv-1.10.1-1.el6.noarch 4/17
Verifying : tkinter-2.6.6-66.el6_8.x86_64 5/17
Verifying : 1:tcl-8.5.7-6.el6.x86_64 6/17
Verifying : augeas-libs-1.0.0-10.el6.x86_64 7/17
Verifying : httpd-tools-2.2.15-60.el6.centos.4.x86_64 8/17
Verifying : redhat-rpm-config-9.0.3-51.el6.centos.noarch 9/17
Verifying : httpd-2.2.15-60.el6.centos.4.x86_64 10/17
Verifying : 1:tix-8.4.3-5.el6.x86_64 11/17
Verifying : ca-certificates-2017.2.14-65.0.1.el6_9.noarch 12/17
Verifying : python-tools-2.6.6-66.el6_8.x86_64 13/17
Verifying : redhat-rpm-config-9.0.3-42.el6.centos.noarch 14/17
Verifying : httpd-tools-2.2.15-54.el6.centos.x86_64 15/17
Verifying : ca-certificates-2014.1.98-65.0.el6_5.noarch 16/17
Verifying : httpd-2.2.15-54.el6.centos.x86_64 17/17
Installed:
augeas-libs.x86_64 0:1.0.0-10.el6 libffi-devel.x86_64 0:3.0.5-3.2.el6 mod_ssl.x86_64 1:2.2.15-60.el6.centos.4 python-tools.x86_64 0:2.6.6-66.el6_8 python-virtualenv.noarch 0:1.10.1-1.el6
Dependency Installed:
tcl.x86_64 1:8.5.7-6.el6 tix.x86_64 1:8.4.3-5.el6 tk.x86_64 1:8.5.7-5.el6 tkinter.x86_64 0:2.6.6-66.el6_8
Updated:
ca-certificates.noarch 0:2017.2.14-65.0.1.el6_9 redhat-rpm-config.noarch 0:9.0.3-51.el6.centos
Dependency Updated:
httpd.x86_64 0:2.2.15-60.el6.centos.4 httpd-tools.x86_64 0:2.2.15-60.el6.centos.4
Complete!
Creating virtual environment...
Installing Python packages...
Installation succeeded.
/root/.local/share/letsencrypt/lib/python2.6/site-packages/cryptography/__init__.py:26: DeprecationWarning: Python 2.6 is no longer supported by the Python core team, please upgrade your Python. A future version of cryptography will drop support for Python 2.6
DeprecationWarning
letsencrypt-auto [SUBCOMMAND] [options] [-d DOMAIN] [-d DOMAIN] ...
Certbot can obtain and install HTTPS/TLS/SSL certificates. By default,
it will attempt to use a webserver both for obtaining and installing the
certificate. The most common SUBCOMMANDS and flags are:
obtain, install, and renew certificates:
(default) run Obtain & install a certificate in your current webserver
certonly Obtain or renew a certificate, but do not install it
renew Renew all previously obtained certificates that are near expiry
-d DOMAINS Comma-separated list of domains to obtain a certificate for
--apache Use the Apache plugin for authentication & installation
--standalone Run a standalone webserver for authentication
--nginx Use the Nginx plugin for authentication & installation
--webroot Place files in a server's webroot folder for authentication
--manual Obtain certificates interactively, or using shell script hooks
-n Run non-interactively
--test-cert Obtain a test certificate from a staging server
--dry-run Test "renew" or "certonly" without saving any certificates to disk
manage certificates:
certificates Display information about certificates you have from Certbot
revoke Revoke a certificate (supply --cert-path)
delete Delete a certificate
manage your account with Let's Encrypt:
register Create a Let's Encrypt ACME account
--agree-tos Agree to the ACME server's Subscriber Agreement
-m EMAIL Email address for important account notifications
More detailed help:
-h, --help [TOPIC] print this message, or detailed help on a topic;
the available TOPICS are:
all, automation, commands, paths, security, testing, or any of the
subcommands or plugins (certonly, renew, install, register, nginx,
apache, standalone, webroot, etc.)
对于好长好长的这种我都习惯去输出一下返回值
[root@why letsencrypt]# echo $?
0
生成证书
- webroot-path为网站的根目录
- d为域名
- email是用于收取邮件的邮箱
[root@why letsencrypt]# ./letsencrypt-auto certonly --webroot --webroot-path /opt/openresty/nginx/html -d www.whysdomain.com --agree-tos --email why@whysdomain.com
/root/.local/share/letsencrypt/lib/python2.6/site-packages/cryptography/__init__.py:26: DeprecationWarning: Python 2.6 is no longer supported by the Python core team, please upgrade your Python. A future version of cryptography will drop support for Python 2.6
DeprecationWarning
Saving debug log to /var/log/letsencrypt/letsencrypt.log
-------------------------------------------------------------------------------
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about EFF and
our work to encrypt the web, protect its users and defend digital rights.
-------------------------------------------------------------------------------
(Y)es/(N)o: Y
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for www.whysdomain.com
Using the webroot path /opt/openresty/nginx/html for all unmatched domains.
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live/www.whysdomain.com/fullchain.pem. Your cert
will expire on 2017-10-26. To obtain a new or tweaked version of
this certificate in the future, simply run letsencrypt-auto again.
To non-interactively renew *all* of your certificates, run
"letsencrypt-auto renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@why letsencrypt]# ll /etc/letsencrypt/
total 24
drwx------ 3 root root 4096 Jul 28 14:42 accounts
drwx------ 3 root root 4096 Jul 28 14:42 archive
drwxr-xr-x 2 root root 4096 Jul 28 14:42 csr
drwx------ 2 root root 4096 Jul 28 14:42 keys
drwx------ 3 root root 4096 Jul 28 14:42 live
drwxr-xr-x 2 root root 4096 Jul 28 14:42 renewal
[root@why letsencrypt]# ll /etc/letsencrypt/live/www.whysdomain.com/
total 4
lrwxrwxrwx 1 root root 42 Jul 28 14:42 cert.pem -> ../../archive/www.whysdomain.com/cert1.pem
lrwxrwxrwx 1 root root 43 Jul 28 14:42 chain.pem -> ../../archive/www.whysdomain.com/chain1.pem
lrwxrwxrwx 1 root root 47 Jul 28 14:42 fullchain.pem -> ../../archive/www.whysdomain.com/fullchain1.pem
lrwxrwxrwx 1 root root 45 Jul 28 14:42 privkey.pem -> ../../archive/www.whysdomain.com/privkey1.pem
-rw-r--r-- 1 root root 543 Jul 28 14:42 README
- cert.pem Apache服务器端证书
- chain.pem Apache根证书和中继证书
- fullchain.pem Nginx所需要ssl_certificate文件
- privkey.pem 安全证书KEY文件
对于nginx就需要使用到fullchain.pem和privkey.pem两个证书文件
生成2048位DH paramenters
Nginx在Ephemeral Diffiel-Hellman的过程中会
[root@why letsencrypt]# ll /etc/ssl/certs/
ca-bundle.crt ca-bundle.trust.crt localhost.crt make-dummy-cert Makefile renew-dummy-cert
[root@why letsencrypt]# openssl dhparam -out /etc/ssl/certs/dhparams.pem 2048
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
.....................................+.................................................................+....................................................+.......................+.............................................................................................................................................+......................................................+.......................................+.................................+.........................................................+.................................+...............................................+..........................................+...+..............................................................+............+....................................+.......................................................+....................................................................................................................+.......................+.......................................+.............................................................+..........................................................................................................................................................+.................................................................................................+..........................................................................+...............................+................................................................................+.............................+................................................................................................................................+.+....+........+........................................................................................................+.....................................................................................................................................................+................................................................................................................................................................+.................................................................................................................................................................................................................................................+..............+..................+...+......................................................................................+............................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................+......+...........................+...................................................................................................................................................................................+...................................................................................................................................................................................................................................................................................................................+............................................................++*++*
配置SSL证书
第一个server是对http请求做https请求跳转,第二个是https的配置
server {
listen 80;
server_name www.whysdomain.com;
return 301 https://$server_name$request_uri;
#location / {
# proxy_pass http://why_real_servers;
# proxy_set_header HOST $host;
#}
}
server {
listen 443 ssl;
server_name www.whysdomain.com;
ssl_certificate /etc/letsencrypt/live/www.whysdomain.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/www.whysdomain.com/privkey.pem;
ssl_dhparam /etc/ssl/certs/dhparams.pem;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA';
ssl_prefer_server_ciphers on;
# Load configuration files for the default server block.
#include /etc/nginx/default.d/*.conf;
location / {
#index index.html;
#head 301
#include fastcgi_params;
#if ($request_method ~ 'HEAD') {
# return 301;
#}
#uwsgi
#include uwsgi_params;
#uwsgi_pass 127.0.0.1:8000;
#http
proxy_pass http://why_real_servers;
proxy_set_header HOST $host;
}
更多ssl配置方式 http://www.jb51.net/article/68452.htm
安全度检验
https://www.ssllabs.com/ssltest/analyze.html
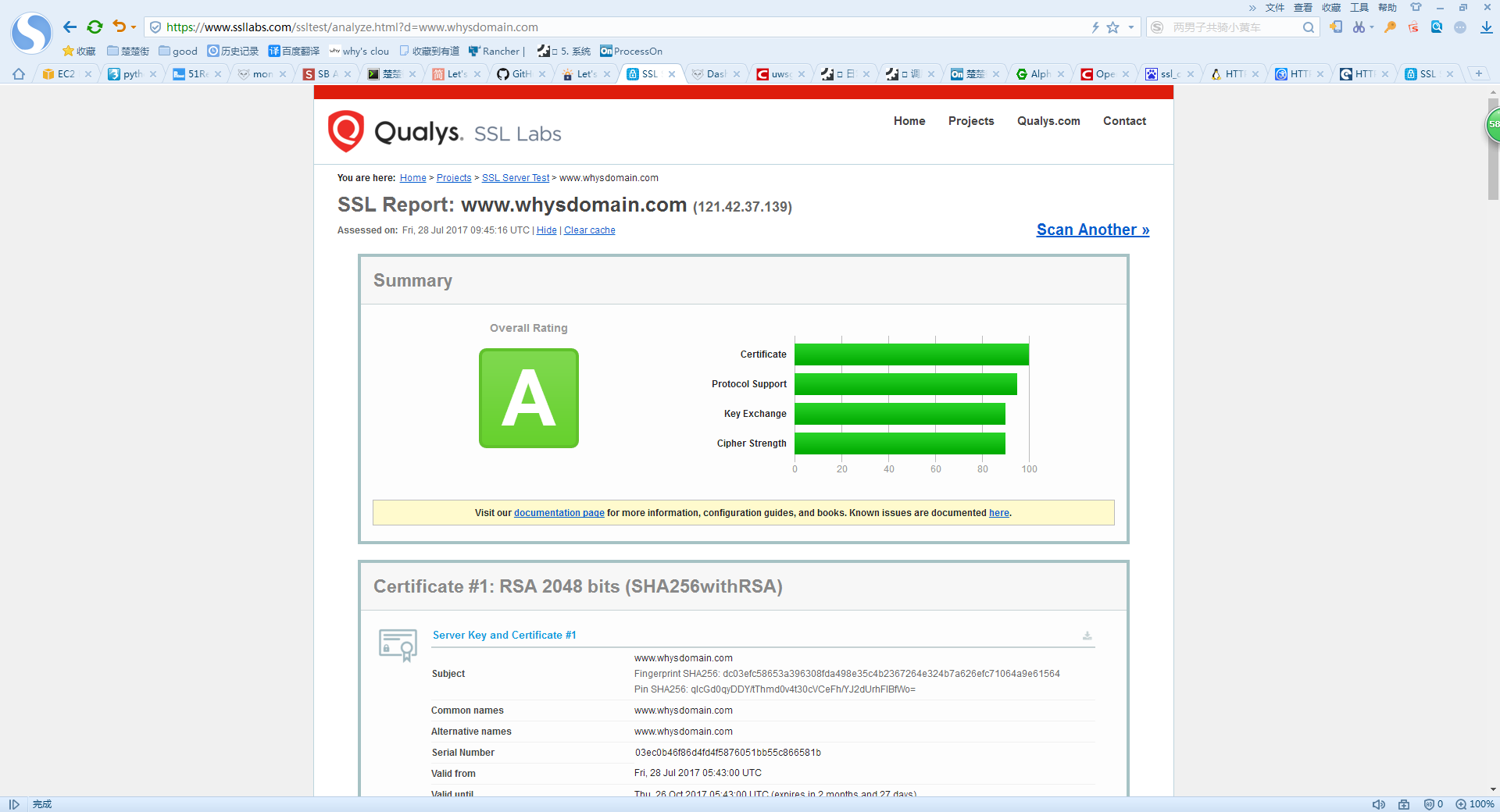
更详细的方式可以参考 http://www.jianshu.com/p/eaac0d082ba2

